Ethical Hacker

Ethical Hacker Training
This Certified Ethical Hacking online course created by top ethical hackers from top organizations will help you learn a wide range of skills such as penetration testing, working with firewalls and intrusion detection systems, and more. You will learn Ethical hacking from scratch. Ethical hacking is an authorized practice that bypasses system security to identify potential data breaches and network vulnerabilities. The company that owns the system or network allows cybersecurity engineers to perform these activities to test the system's security. So, unlike malicious hacking, this process is planned, authorized, and, most importantly, legal. This Ethical hacker training program will help you master all techniques and concepts necessary and help you land demanding and high paying certified ethical hacker jobs.
Course Overview
QTS provides you with the complete Ethical Hacking course from beginner to advance. During the course, you will work on real-world scenarios to gain practical knowledge of intrusion detection systems, sniffing, DoS attacks, and honeypots. Students will master advanced ethical hacking concepts such as SQL injections, wireless network, and mobile platform hacking, IoT hacking, and cryptography in this course.
This training module will give you a real chance in taking and clearing Ethical Hacking certification effortlessly. Our live instructor-led classes and flexible schedules make it interesting for you. We also provide a certified ethical hacker study guide that covers all the essential topics. By the end of the course, you will become proficient in ethical hacking concepts and be industry-ready.
Ethical Hacking Certification Key Features
- Introduction to Ethical Hacking
- Get Ethical Hacking Certification
- Mock tests, Mock interviews
- Real-time projects for practice
- 24/7 support to solve your queries
- Schedule your timing as per your convenience
- One on One sessions
Who should Learn Ethical Hacking?
This course is ideal for IT security officers, network specialists, systems engineers, network engineers, IS/IT specialists and analysts who either want to enhance their skillset or shift to the ethical hacking domain. Freshers who want to learn ethical hacking can also opt for this course.
Top Hiring Company
Industry Trends
Course curriculum / Syllabus
- Overview of Information Security
- Understanding Information Security Threats and Attack Vectors
- Penetration Testing Concepts
- In-depth knowledge of Hacking Concepts
- Ethical Hacking Concepts
- Workings of Information Security Controls
- Information Security Laws and Standards
- Understanding Footprinting Concepts
- Concepts of Footprinting through Search Engines
- Concepts of Footprinting through Web Services
- Footprinting through Social Networking Sites
- Wokrings of Website Footprinting
- Workings of Email Footprinting
- What is Competitive Intelligence?
- Define Whois Footprinting?
- Workings of DNS Footprinting
- Workings of Network Footprinting
- Footprinting through Social Engineering
- Workings of Footprinting Tools
- Footprinting Countermeasures
- Understanding Footprinting Pen Testing
- Network Scanning Concepts
- How to use Scanning Tools?
- In-depth knowledge of Scanning Techniques
- Detialing of Scanning Beyond IDS and Firewall
- What is Banner Grabbing?
- Draw Network Diagrams
- Understanding Scanning Pen Testing
- Network Scanning Concepts
- How to use Scanning Tools?
- In-depth knowledge of Scanning Techniques
- Detialing of Scanning Beyond IDS and Firewall
- What is Banner Grabbing?
- Draw Network Diagrams
- Understanding Scanning Pen Testing
- Enumeration Concepts
- What is NetBIOS Enumeration?
- What is SNMP Enumeration?
- Workings of LDAP Enumeration
- Workings of NTP Enumeration
- Understanding SMTP Enumeration and DNS Enumeration
- Enumeration Countermeasures
- Exploring other Enumeration Techniques
- What is Enumeration Pen Testing?
- Vulnerability Assessment Concepts
- Vulnerability Assessment Solutions
- Vulnerability Scoring Systems
- Vulnerability Assessment Tools
- Vulnerability Assessment Reports
- System Hacking Concepts
- Conepts of Cracking Passwords
- Workings of Privileges
- Executing Applications
- Workings of Hiding Files
- Covering Tracks
- Understanding Penetration Testing
- Malware Concepts
- Understanding Trojan Concepts
- Virus and Worm Concepts
- Malware Analysis
- Malware Countermeasures
- Anti-Malware Software
- Malware Penetration Testing
- Sniffing Concepts
- Sniffing Technique: Understanding MAC Attacks
- Sniffing Technique: Understanding DHCP Attacks
- Sniffing Technique: What is ARP Poisoning?
- Sniffing Technique: Analysis of Spoofing Attacks
- Sniffing Technique: Analysis of DNS Poisoning
- Workings of Sniffing Tools
- Sniffing Countermeasures
- Sniffing Detection Techniques
- Understanding sniffing Pen Testing
- Social Engineering Concepts
- Social Engineering Techniques
- Analysis of Insider Threats
- Impersonation on Social Networking Sites
- What is Identity Theft?
- Social Engineering Countermeasures
- Understanding Social Engineering Penetration Testing
- DDoS/DoS Concepts
- DDoS/DoS Attack Techniques
- What is Botnets?
- DDoS Case Studies
- Workings of DDoS/DoS Attack Tools
- DDOS Counter measures
- How to use DDoS/DoS Protection Tools?
- Understanding DDoS/DoS Attack Penetration Testing
- Session Hijacking Concepts
- Understanding Application Level Session Hijacking
- Understanding Network Level Session Hijacking
- Workings of Session Hijacking Tools
- Session Hijacking Countermeasures
- What is Penetration Testing
- Understanding IDS, Firewall, and Honeypot Concepts
- Understanding IDS, Firewall, and Honeypot Solutions
- Concepts of Evading IDS
- How to Evade Firewalls?
- Workings of Firewall/IDS Evading Tools
- Methods of Detecting Honeypots
- Firewall/IDS Evasion Countermeasures
- Penetration Testing
- Web Server Concepts
- Understanding Web Server Attacks
- Web Server Attack Methodology
- Workings of Web Server Attack Tools
- Web server attack Countermeasures
- Patch Management
- Workings of Web Server Security Tools
- What is Web Server Pen Testing?
- Web App Concepts
- Understanding Web App Threats
- Hacking Methodology
- Workings of Web Application Hacking Tools
- Web app hacking Countermeasures
- Workings of Web App Security Testing Tools
- Understanding Web App Pen Testing
- SQL Injection Concepts
- Types of SQL Injection
- SQL Injection Methodology
- Workings of SQL Injection Tools
- Understanding Evasion Techniques
- SQL injection countermeasures
- Wireless Concepts
- Wireless Encryption
- Understanding Wireless Threats
- Wireless Hacking Methodology
- Workings of Wireless Hacking Tools
- Bluetooth Hacking
- Wireless hacknig countermeasures
- Workings of Wireless Security Tools
- Understanding Wi-Fi Pen Testing
- Mobile Platform Attack Vectors
- Analysis of hacking Android OS
- Understanding of hacking iOS
- Using Mobile Spyware
- What is Mobile Device Management?
- Understanding Mobile Security Guidelines and Tools
- What is Mobile Pen Testing?
- IoT Concepts
- Understanding of IoT Attacks
- IoT Hacking Methodology
- Workings of IoT Hacking Tools
- IOT hacking Countermeasures
- Understanding IoT Pen Testing
- Cloud Computing Concepts
- Cloud Computing Threats
- Cloud Computing Attacks
- Analysis of Cloud Security
- Workings of Cloud Security Tools
- Understanding Cloud Penetration Testing
- Cryptography Concepts
- Encryption Algorithms
- Workings of Cryptography Tools
- Overview of Public Key Infrastructure (PKI)
- Detailed understanding of Email Encryption
- Detailed understanding of Disk Encryption
- Cryptanalysis
- Cryptography Countermeasures
Ethical Hacker FAQ’s:
Ethical hacking is an authorized practice that bypasses system security to identify potential data breaches and network vulnerabilities. The company that owns the system or network allows cybersecurity engineers to perform these activities to test the system's security.
Ethical hacking is an authorized practice that bypasses system security to identify potential data breaches and network vulnerabilities. The company that owns the system or network allows cybersecurity engineers to perform these activities to test the system's security.
The EC council provides the certification, and the duration of the exam is 4 hours. CEH is the prefix of the exam. We will provide the necessary support through the registration process.
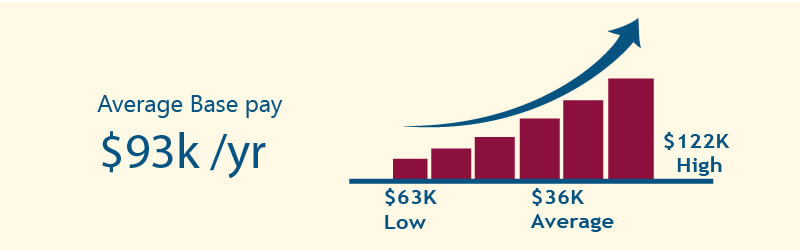
The average salary of certified ethical hacker is $99,658/yr.
The exam format is multiple choice of questions. It is the proctored exam conducted online or at VUE test centres.
Yes, we do provide a certificate upon completion of the course successfully. Our certificate is industry-recognized and will help you gain credibility among the companies hiring.
We would provide you with the missed recording session and also eLearning material for self-study
Yes, you can attend the demo and clear all your hesitations from the experts.
Yes, we do provide job placement services.
Enquire Now
Related Courses
Why QTS INFO
Best Virtual training classrooms for IT aspirants
Real time curriculum with job oriented training.
Around the clock assistance
We are eager to solve your queries 24*7 with help of our expert faculty.
Flexible Timings
Choose your schedule as per your convenience. No need to delay your work
Mock projects
Real world project samples for practical sessions



